From enabling remote access to corporate networks to securing site-to-site connections, Virtual private networks (VPNs) have become increasingly essential in today’s security-conscious networking industry.
As their usage grows, so does the need for greater observability and visualization of VPN performance. Real-time monitoring of performance, security, efficiency, and compliance has become a significant aspect of VPN operations.
This article explores best practices in VPN monitoring that can be used to ensure optimal end-to-end performance, security, and reliability in modern network environments.
Summary of key VPN monitoring concepts
The following table contains a list of concepts and best practices in the context of VPN monitoring that will be further examined in this article.
Before discussing the above concepts, let's briefly review VPN fundamentals as core VPN operations impact monitoring.
Understanding VPNs
A VPN is a technology for securely transmitting data over any network by encapsulating it within additional headers. The headers are added to establish secure tunnels between two endpoints. Tunneling refers to encapsulating packets within other packets before transmitting them over a public or untrusted network, such as the Internet. Encryption ensures that even if data is intercepted, it remains unreadable without proper decryption credentials. Thus, the VPN ensures that only authorized and authenticated parties can access and interpret the transmitted information.
Types of VPNs
VPNs can be categorized based on their purpose, architecture, and deployment methods.
- Remote access VPN enables individual users to securely connect to a private corporate or enterprise network over the Internet from a single end device, such as a PC or mobile phone.
- Site-to-site VPN is used to interconnect remote networks to each other, typically a branch office network to headquarters.
- Cloud VPN securely connects on-premises network infrastructure to cloud environments.
Operations
The following diagram shows one particular use case: a PC running a VPN client connects to a VPN server over an untrusted network.
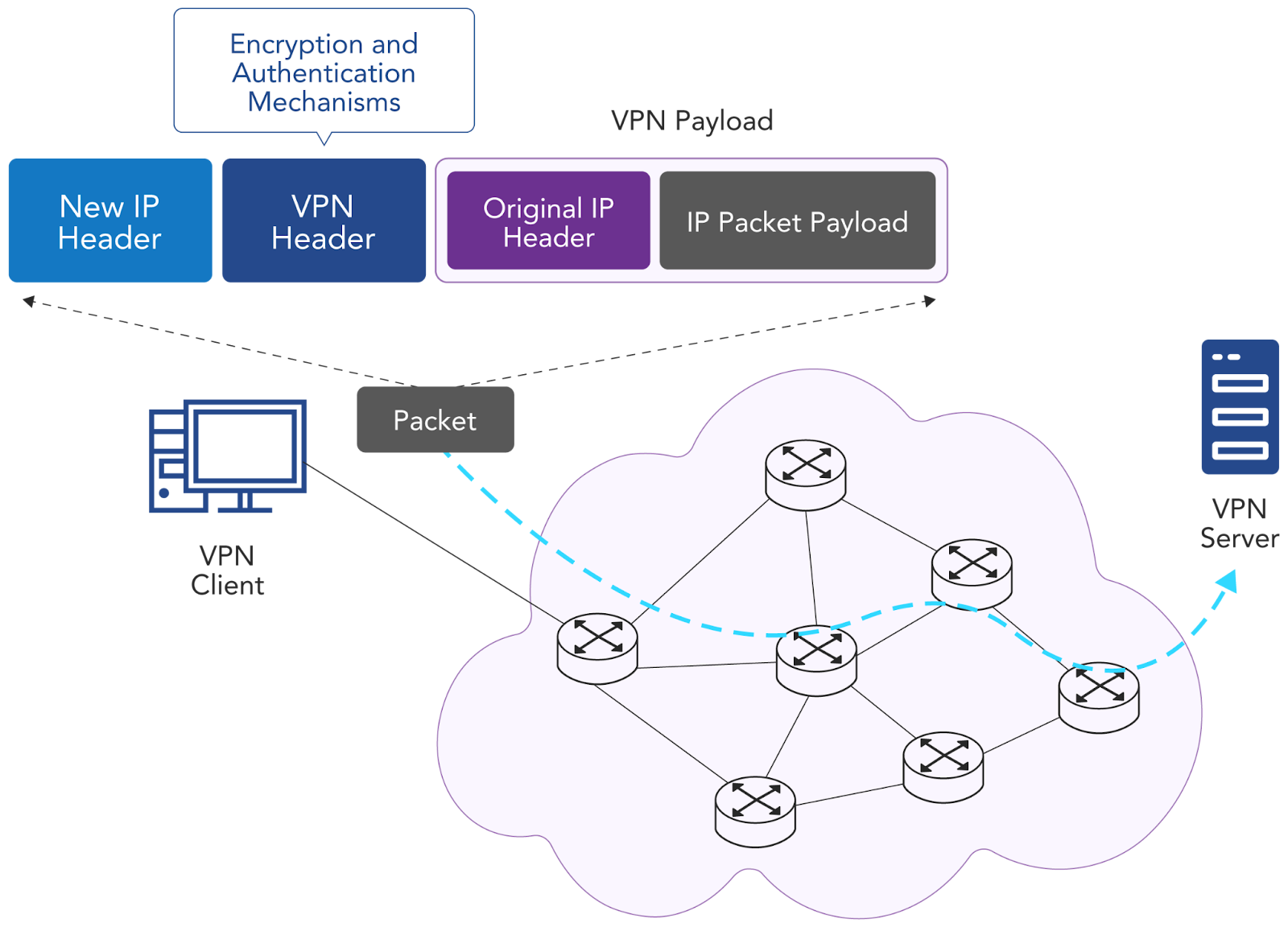
Initially, the VPN client establishes a tunnel between itself and the VPN server. Initial communication between the client and server authenticates the client. The server and client agree upon the methods they will use for encapsulation and encryption. Once a successful agreement is reached, the tunnel is considered established.
When the VPN client sends traffic to the server, it takes the original IP packet and encapsulates it as the VPN tunnel payload. A VPN header is prepended to the original IP packet with a new IP header containing the destination IP address of the VPN server. The VPN header includes the necessary information to encrypt the original IP packet on egress from the VPN client and decrypt it on ingress to the VPN server based on the initial agreement between the two entities.
The original IP packet is encrypted, encapsulated, and transported to the VPN server based on the new outer IP header. During transport over the untrusted network, the payload remains confidential. Once it reaches the VPN server, it is decapsulated, decrypted, and sent to its final intended destination based on the original IP header.
VPN protocols and encryption methods
A wide variety of protocols are used to tunnel and encrypt data using VPNs. The methodologies must be agreed upon between the entities acting as VPN endpoints. The methods vary significantly in security level, degree of overhead, complexity, and availability.
VPN protocols:
- IPsec (Internet Protocol Security)
- SSL/TLS VPN (Secure Sockets Layer / Transport Layer Security)
- OpenVPN
- WireGuard
- L2TP/IPsec (Layer 2 Tunneling Protocol with IPsec)
- PPTP (Point-to-Point Tunneling Protocol)
- IKEv2/IPsec (Internet Key Exchange v2)
- SoftEther VPN
- SSTP (Secure Socket Tunneling Protocol)
- MPLS VPN
Encryption methods:
- AES (Advanced Encryption Standard) – AES-128, AES-192, AES-256
- ChaCha20
- Blowfish
- 3DES (Triple Data Encryption Standard)
- Camellia
- RSA (Rivest-Shamir-Adleman)
- ECC (Elliptic Curve Cryptography)
- DH (Diffie-Hellman Key Exchange)
- ECDH (Elliptic Curve Diffie-Hellman)
- SHA (Secure Hash Algorithm) – SHA-1, SHA-256, SHA-512
The above list highlights the extensive range of available VPN protocols and encryption methods, emphasizing the added complexity involved in their deployment.
Limitations
The primary disadvantage of VPNs is that they add several types of overhead that can impact network performance and resource utilization.
Encryption overhead
VPN encryption algorithms require additional processing power. The stronger the encryption algorithm, the more CPU resources are consumed, potentially reducing the performance of network devices.
Encapsulation overhead
VPN protocols encapsulate packets with additional headers, which increase the total packet size. This leads to higher bandwidth consumption and potential fragmentation, especially if the packet size exceeds the underlying network infrastructure's Maximum Transmission Unit (MTU).
Latency overhead
The steps involved in encapsulating, encrypting, decrypting, and decapsulating data introduce delays, which increase latency.
Management overhead
VPNs add complexity to any network, resulting in management, administration, and maintenance overhead.
VPN monitoring fundamentals
The benefits that VPNs deliver, combined with their limitations and complexities, make VPN monitoring even more important.
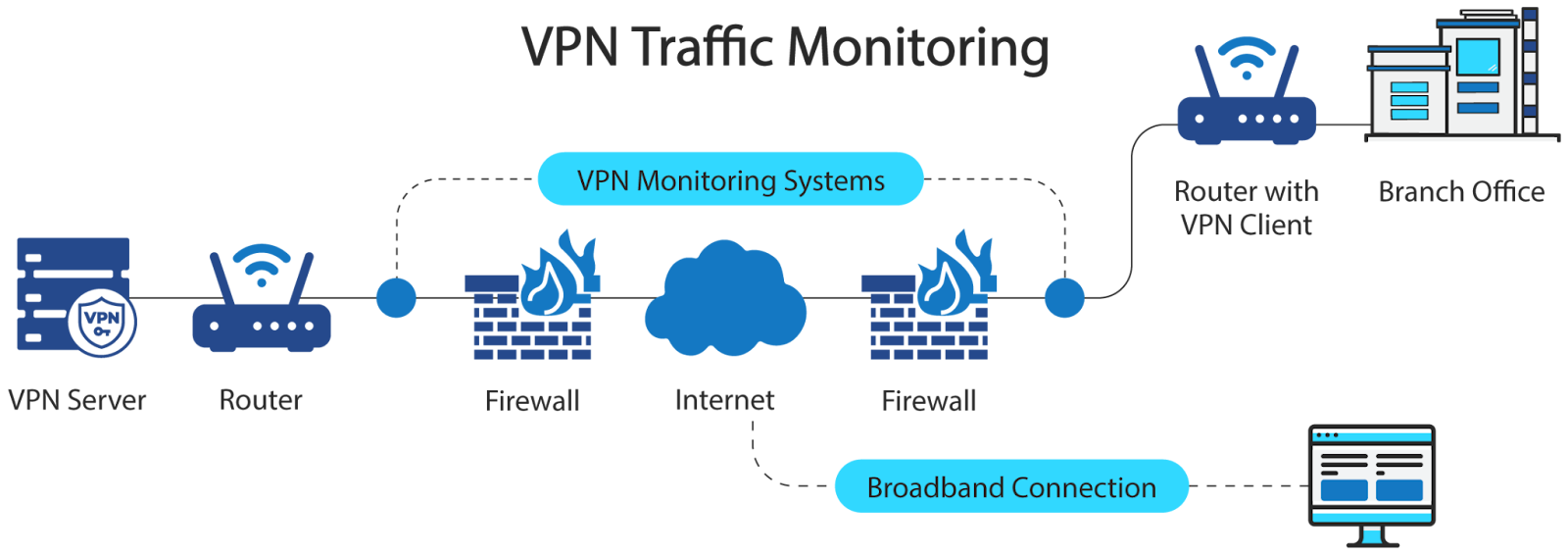
Real-time VPN performance monitoring
Monitoring VPN performance metrics like latency, throughput, and packet loss helps network administrators quickly detect and respond to performance degradation. Proactive monitoring helps identify issues such as congestion or jitter that impact VPN reliability and the user experience.
Effective VPN management must extend beyond the tunnel itself, as it requires visibility into both ends of the VPN. Monitoring remote endpoints, VPN gateways, and the data center and cloud infrastructure used by VPNs is necessary to ensure end-to-end security and performance. In this way, compliance can be maintained, and VPN operations can be optimized, especially for mission-critical applications.
Internet path analysis
Internet path analysis is a method by which public Internet segments that can impact VPN performance are monitored and evaluated. Since VPNs primarily depend upon the Internet for transport, various factors, including BGP routing, network congestion, and suboptimal path selection, affect the effectiveness of VPNs, including latency and reliability. Route changes, traffic blackholing, and ISP-level disruptions that can potentially degrade VPN connectivity can be detected and mitigated.
Catchpoint’s Internet Performance Monitoring (IPM) solution delivers the necessary deep visibility into these public network paths, helping to identify troublesome areas and optimize route selection to ensure a stable and high-performing VPN user experience.
Synthetic testing and VPNs
Compared to passive monitoring, which relies on real traffic, synthetic testing generates controlled test traffic to evaluate very specific metrics. It simulates real user interactions to assess performance, availability, and reliability, giving more control and detecting issues before they affect actual users.
Synthetic testing helps identify issues across various locations and endpoints when used with VPNs. It can also be an important part of an organization’s strategy for validating VPN SLAs.
Security and SLA compliance
VPNs are prime targets for threats such as man-in-the-middle attacks, unauthorized access, and traffic hijacking, making continuous surveillance essential. VPN SLA compliance requires tracking key performance indicators, including uptime, latency, packet loss, and throughput, to ensure providers meet agreed-upon standards. This is especially true for mission-critical services such as site-to-site and cloud VPNs.
However, increasing the security level has a trade-off in VPN performance— the more secure encryption methods typically have a greater impact on latency and performance. Thus, security monitoring must be coupled appropriately with SLA compliance monitoring to ensure that both performance and security requirements are met.
Combining security evaluation with performance analytics strengthens network integrity and service reliability, ensuring the secure and efficient operation of VPNs of all types.
Integration with other monitoring tools
VPN monitoring should become part of an organization’s broader monitoring, visualization, and observability strategy. It should be integrated with network performance monitoring (NPM), security information and event management systems (SIEMs), and application performance monitoring (APM) platforms. A holistic approach ensures that VPN metrics are not collected and analyzed in isolation but are used as part of the broader network and security ecosystem.
Today, organizations are adopting secure access service edge (SASE) architectures and replacing or augmenting VPNs with zero-trust and cloud-based security models. This trend of moving from VPN to SASE necessitates the evolution of VPN monitoring systems, which must accommodate a more dynamic identity-driven security model.
SASE integrates zero trust principles, cloud-based security, and software-defined networking. These aspects must be considered when employing VPN monitoring today to ensure that today’s monitoring strategies are well aligned with SASE frameworks for future transitions. As such, the future of VPN monitoring must evolve towards converged visibility across all network environments, including on-premises, hybrid, and cloud infrastructures.
Last thoughts
VPN monitoring is an integral part of a holistic network monitoring approach. Network performance, security, and reliability are key elements of a successfully deployed and operational network. By continuously obtaining visibility into latency, throughput, security threats, and compliance metrics, organizations can ensure secure and high-performance connectivity for their users.
As enterprises transition their networks to using SASE and zero-trust security models, tools such as Catchpoint’s IPM solution become all the more important. To stay ahead of such network challenges, explore Catchpoint’s comprehensive monitoring tools and take your VPN strategy to the next level.

