Network administrators use various remote desktop tools for routine maintenance, application deployment, performance troubleshooting, and end-user support. From system administrators troubleshooting a user’s PC to employees working from home and third-party vendors accessing client environments, remote desktop tools have become foundational in modern ICT operations.
As these tools become more prevalent, the need for oversight increases, particularly regarding security compliance. Remote desktop monitoring is critical to ensure sessions are secure, conformant, and compliant with internal policies and external regulations.
This article examines remote desktop monitoring use cases and best practices to manage and secure remote desktop sessions effectively.
Summary of key remote desktop monitoring best practices
Applications of remote desktop services
Remote desktop services enable a series of possibilities for network administrators and business employees.
Network administration tools
Remote desktop services enable network administrators to remotely access employee computers. They can recreate troubleshooting steps that more directly deal with the user's network problems. Similarly, they can install and configure software programs remotely, saving time and reducing transportation costs for a geographically dispersed workforce.
Vendors or software experts can also conduct one-on-one remote training using remote desktop services, making such training much more efficient.
Remote and hybrid workforce
Organizations use remote desktop services to provide remote and hybrid work environments, allowing employees to work remotely or on-site using the same device. Employees can log in to their office computers remotely to work on the same device with the same settings, network services, and setup, regardless of where they are.
Remote Desktop as a Service (DaaS/RDS) is a cloud-based service that provides users access to a virtual desktop environment hosted in the cloud. Instead of running a desktop operating system and applications on a physical machine, everything runs over cloud infrastructure, and the user connects remotely over the Internet. The same virtual environment is available whether the user is in the office, at home, or on the go.
Remote desktop monitoring best practices
As remote desktop services become increasingly prevalent and integral to mission-critical systems, remote desktop monitoring becomes even more critical. It should be included as an integral part of a more comprehensive network monitoring strategy.
Consider the following best practices for remote desktop monitoring.
Log and audit remote desktop sessions
Logging and auditing remote desktop sessions provide visibility into who is accessing systems, when and where they are being accessed, and what actions are being performed during those sessions. Detailed logging is integral to security, accounting and forensic investigations. It is also necessary to meet compliance requirements like SO 27001, HIPAA, or PCI-DSS.
Most remote desktop services offer extensive built-in logging systems and features, including the ability to store logs locally or send them to centralized log servers or third-party Security Information and Event Management (SIEM) platforms. Third-party monitoring tools greatly enhance logging capabilities by capturing more granular activity and cross-referencing it with other logged network events.
Capture the following data in your logs:
- User identity and authentication method
- Time of connection and disconnection
- IP address and device used
- Applications accessed and files transferred
- Failed login attempts and duration of sessions
- Privilege level of user (admin, user, guest)
Monitor session performance metrics
Remote sessions in mission-critical and high-traffic environments can suffer from lag, freezing, or disconnection. Monitoring session performance metrics is essential for ensuring a smooth and reliable user experience while maintaining system efficiency. This is the case regardless of the remote desktop tool and its application.
Key metrics to monitor include:
- CPU - detects resource-heavy applications or “misbehaving” processes.
- Memory - identifies memory leaks or excessive RAM consumption.
- Disc I/O - highlights slow disc performance that may affect user sessions.
- Network bandwidth - detects bottlenecks, especially in network-constrained environments during file transfers
However, it is not always intuitively apparent on what specific systems the metrics in question should be monitored. The answer depends upon your unique implementation. For example:
- The virtual machine must be monitored in virtual desktop infrastructure environments such as Citrix or Azure Virtual Desktop.
- The RDS server must be monitored in Remote Desktop Services (RDS), as multiple users may connect to it concurrently.
- Available resources in the cloud system allocated to the user must be monitored for cloud-hosted systems that fall within an RDaaS implementation.
Bandwidth utilization is among the most crucial metrics, as the entire user experience, including screen rendering, keystrokes, and audio, is transmitted over the network. Keeping an eye on these metrics helps ICT teams identify and resolve problems early. They can identify if a system is using too many resources, a software configuration has gone wrong, or a network connection is not performing as expected.
A great example of this kind of monitoring is Catchpoint’s platform. It stands out by delivering real, actionable insights into DaaS user experiences—no matter where your users are or which provider you use. With intelligent observability that goes deep and wide, Catchpoint provides a comprehensive view of your DaaS environment. That means your IT team can spot issues fast and keep everything running smoothly for everyone, everywhere..
Real-time session monitoring
With real-time monitoring, ICT teams can monitor remote desktop sessions as they occur, responding immediately if anything appears out of the ordinary. It’s a hands-on approach going beyond the traditional review of logs and reports. It provides administrators with the opportunity to identify and address issues as they arise.
Real-time session monitoring can take various forms.
- Active session listings provide a real-time view of currently active and connected users, including their session states.
- Usage stats and health metrics display each session's live resource usage and network latency.
- Live session view lets administrators see what the user sees in real-time.
- Session shadowing enables network technicians to take control of a session or assist the user within the context of IT support.
Real-time session monitoring also helps detect unauthorized live session views or session shadowing. While useful for support and training, shadowing can be misused for more malicious purposes if it is done without user consent or proper logging.
Remote desktop monitoring alerts
In conjunction with real-time session monitoring, automatic alerts are an essential part of monitoring remote desktop sessions. You can configure alerts to automatically notify administrators or trigger automated responses from network monitoring and security systems. They can mitigate security risks and minimize the potential damage from unusual or unexpected events.
Alerts should be set for events such as the ones listed below.
- Long, idle, or unusually short sessions
- Attempted connections from blacklisted IPs or devices
- Use of unexpectedly elevated privileges or access to sensitive resources
- Multiple failed login attempts, as they may indicate a brute-force attack
Time-based alerts can be configured to identify remote access during off-hours or from unexpected locations. When appropriate alerts are configured, automated systems and ICT teams can respond quickly before an issue escalates into a breach or outage.
Remote desktop monitoring as part of a broader monitoring strategy
Remote desktop monitoring should not be deployed within a silo but should be integrated into a centralized security and operations framework. Most organizations already have some level of tracking for their networks and systems, such as a Security Information and Event Management (SIEM) system. You can integrate remote desktop monitoring with such a system to leverage cross-referencing and correlation of events, identifying and mitigating risks more efficiently.
Integrated remote desktop monitoring results in:
- More straightforward compliance reporting
- Faster and more coherent incident response
- Reduced risk of oversight because of dispersed logs and
- A unified dashboard for system health and security status.
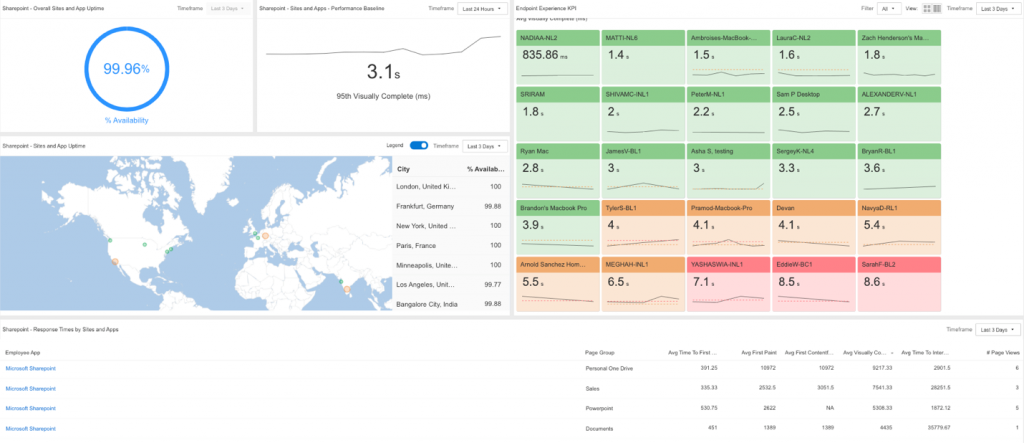
Catchpoint’s solutions are an example of a well-integrated remote desktop monitoring service. You get a more comprehensive approach, where remote desktop monitoring information is analyzed as part of the overall network monitoring data collection. As a result, a more proactive approach can be taken rather than a reactive one.
Periodic review and analysis
Remote desktop monitoring is only as valuable as the insights it produces. Its insights are only helpful if you examine, review, analyze, and evaluate them. Even if no critical events are recorded or indicated, it is crucial to generate reports and review them periodically to understand the current state of the related systems. That way, you can spot important trends, such as potentially underutilized or overburdened systems.
Various tools can be used to periodically analyze accumulated data, including integrated SIEM systems with built-in dashboards, filtering, and visualization capabilities. Use business intelligence (BI) tools to slice session data across time, user, or location and schedule reports that can be sent to IT and compliance teams.
Last thoughts
Remote desktop services are expected to continue playing a critical role in modern organizations. When deployed correctly and comprehensively, remote desktop monitoring helps to ensure the secure, efficient, and compliant use of these services.
Logging and auditing sessions, tracking performance metrics, enabling real-time monitoring and alerts, and integrating them into centralized monitoring tools such as SIEMs are all vital in ensuring safe and robust operations. These best practices help maintain system performance and support user productivity. They also help protect against unauthorized access, data breaches, and compliance violations, all of which are vital in today’s business environments.

