Border Gateway Protocol (BGP) is the Internet's de facto routing protocol. A secure, stable, and fast BGP performance quite naturally remains a key point of concern for most organizations hosting mission-critical services.
Border Gateway Protocol routing is the process by which routes to all destinations worldwide are propagated and shared between network owners and operators. Malfunctions, misconfigurations, and malicious activities are all potential threats to the reliable and resilient functioning of BGP routing.
The wide-scale monitoring of BGP routing processes is vital for ensuring the stability and security of the Internet's operation. Thus, a framework of best practices for ensuring the sound operation of BGP is essential for large-scale enterprises, service providers, and other geographically expansive global players to achieve a high level of BGP observability and keep the Internet operating smoothly.
In this article, we will cover a set of BGP best practices that enable intelligent agents to deliver superior insight into the protocol’s performance, right down to the last mile.
Summary of key BGP routing concepts
The table below summarizes the BGP routing concepts this article will explore in more detail.
BGP routing monitoring
Monitoring BGP routing is a daunting task. To claim global coverage, it requires more than a handful of conveniently placed nodes in cloud regions. For this reason, it is essential to go beyond the distribution of “dumb” nodes and instead deploy intelligent agents. These intelligent agents are purpose-built to provide extensive insight into network operations across a diverse mesh of international network providers.
Unlike many service providers that rely on a few cloud-based vantage points that often overlook last-mile issues, the deployment of intelligent agents is a non-negotiable approach. BGP monitoring agents operate close to where users actually are, delivering visibility to the edge and not just the core.
The sections below explore Border Gateway Protocol routing best practices and the use of these intelligent agents in detail.
Monitoring BGP reachability from the edge
What happens when a prefix is reachable from New York but unreachable from Denver? Users in Denver experience the failure firsthand. Even so, such issues may go undetected by traditional cloud-based probes because they are typically located in major data centers or public cloud regions. This clustering is misaligned with end-user experience and can miss localized outages or asymmetric routing anomalies.
To fully observe BGP routing and address such failure modes, monitoring tools must measure reachability from a user-centric vantage point. User-centric monitoring requires visibility of the network's edge, not just its core.
Intelligent agents deployed near and even within last-mile networks, such as in ISPs and user networks, help to provide this visibility. These agents can uncover localized outages, misrouted prefixes, and hijacks early. Their proximity to the end user enables proactive detection before the issue accelerates or spreads across larger geographic regions.
Such deployments provide last-mile insight and proactive detection, which are vital for the continual operation of BGP routing. The monitoring of BGP routing must be built on a foundation of distributed intelligence, enabling the high-resolution detection of anomalies with geo-specific accuracy.
Enforce prefix filtering
Way back in 2008, a Pakistan Telecom autonomous system began making an unauthorized announcement of the 208.65.153.0/24 network. An upstream provider forwarded this advertisement to the rest of the Internet, resulting in a significant global-scale prefix hijacking incident affecting YouTube traffic.
Administrators could have prevented the incident by applying the appropriate prefix filtering policies at key interconnection points. Admins can use filtering to ensure that only expected routes are accepted by peers and customers or are advertised to upstream providers. In this 2008 event, a lack of outbound filtering allowed a misconfigured or malicious announcement to propagate unchecked, impacting millions of users worldwide.
Networks and the global Internet must be protected by limiting advertised (outbound) and accepted (inbound) routes. Inbound filtering protects your network, while outbound filtering protects everyone else. Filtering is a vital part of the process known as “route hygiene” that ensures that Border Gateway Protocol routing announcements (both inbound and outbound) are accurate, secure, and consistent.
Intelligent monitoring of BGP routing plays a crucial role in automated filter validation, which helps prevent accidental leaks and ensures the continuous operation of prefix list auditing and real-time filter validation. As such, filtering is not a “set and forget” approach but an ongoing process that involves monitoring, incident response, and continuous improvement.
Detect and alert on route flaps
By design, BGP is a routing protocol that converges significantly slower than traditional IGPs. While the convergence of individual prefixes may take up to about a minute, convergence across a large geographically dispersed set of autonomous systems may take several minutes or more.
Convergence will take even longer in the event of route flapping. Route flapping occurs when a BGP prefix repeatedly becomes available and then unavailable or continually changes its next-hop or path attributes within a very short period. This can be caused by frequent changes in the topology, a misconfiguration in a BGP router, or a prefix that is continually alternately advertised and then withdrawn.
This results in convergence delay, network instability, multiple BGP update messages being sent across the Internet, increased CPU and memory usage on routers, and routing table churn. Ultimately, this causes potential packet loss and degraded performance for those affected prefixes.
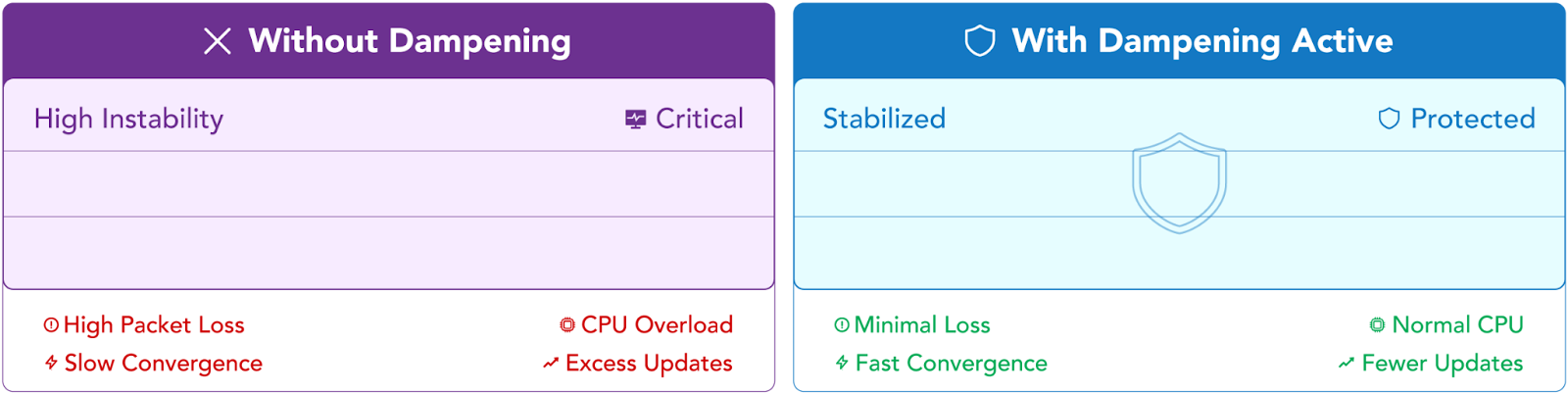
Intelligent agents can help detect flap patterns early, identify which prefixes are unstable, and which ASNs they originate from. Teams can then correlate all this information with user impact and geo-correlated flap alerts, which can be used to intelligently apply automated flap dampening where needed, thereby helping to mitigate the effects of route flapping.
Catchpoint’s robust BGP monitoring empowers teams to detect and address route flaps quickly. For a deep dive into how you can protect against route flapping, check out The Comprehensive Guide to BGP white paper.
Secure BGP sessions and origin validation
A BGP security strategy should take a two-pronged approach. The first involves securing BGP sessions, that is, the communication sessions between BGP peers. The second involves securing the advertised routes using route origin validation.
The first prong, BGP session security, involves the authentication and encryption of BGP sessions between peers. In RFC 2385, MD5 was first introduced for this purpose, but this approach is now considered legacy. It has been replaced by the TCP Authentication Option (TCP-AO) as described in RFC 5925.
Protecting the BGP session in this manner is of utmost importance for the security of the protocol. Malicious attackers can masquerade as BGP peers and can freely inject unauthorized routes into the global Internet routing tables, disrupting communications and redirecting network traffic globally.
The second prong involves route origin validation (ROV). As its name suggests, it is a method of certifying that a received advertised route is indeed sent from an authorized originator. Resource Public Key Infrastructure (RPKI) is a PKI framework that is specifically designed for the validation of BGP routes, helping to strengthen the trustworthiness of BGP routing information. By verifying that the AS announcing the prefix is authorized to do so, threats such as trivial prefix hijacks, where the attacker does not forge the AS path to impersonate another AS, along with accidental leaks, and route misadvertisements are mitigated.
It should also be stressed here that ROV has its challenges as well. If ROV drops a prefix from a leg of routing, it may be dropped for good, resulting in an unreachable network. Although this is preferable to a prefix under attack, it still can cause routing havoc. Thus, having BGP routing monitoring in place to detect and react to such scenarios is all the more important!
Monitoring of BGP routing complements the security provided by both TCP-AO and RPKI by offering visibility into how these security measures function in real-world routing behavior. Monitoring helps detect if sessions are being reset, if invalid routes are still being accepted or propagated after detection, or if suspicious announcements are bypassing policy controls, resulting in a layered approach that ensures that even if a security mechanism fails or is misconfigured, operators are alerted early through observable anomalies in the BGP control plane.
Leverage BGP communities for policy control
BGP communities are an attribute of the protocol typically leveraged to deliver extreme granular policy routing. Communities are used to tag particular routes and influence how they are propagated throughout a network. Observability tools can also leverage this high level of control to monitor the routing process itself.
A network operator may tag certain prefixes with communities to request specific actions from upstream providers, such as AS path prepending, avoiding certain peering points, or preventing further advertisement beyond the provider’s network. This is also known as the well-known “no-export” community.
These communities are simply attributes that are attached to the route itself. Take a look at the following packet capture of a BGP update that contains prefixes with communities.
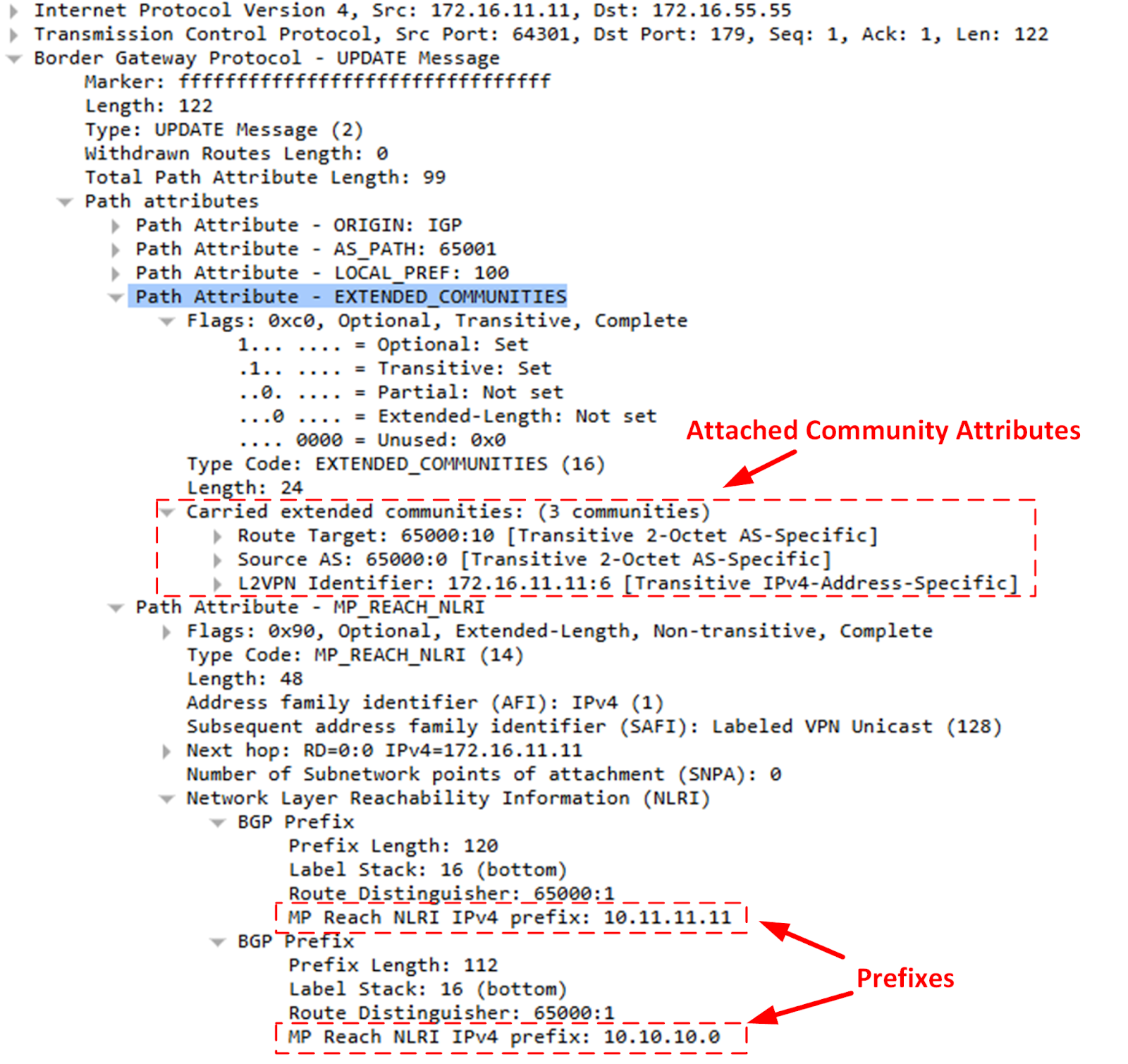
These communities are attributes attached to the prefixes as “additional information” used for policy routing and a series of other BGP-related mechanisms, including virtual routing and forwarding (VRF) and traffic engineering.
Now, these same communities, which can also be thought of as “tags” of additional information, can be used as policy signals guiding routing behavior across complex multi-provider environments without modifying the prefixes themselves.
Network providers can choose to honor these communities or not. Once your routes are advertised outside of the ASes you control, it’s really up to the other network entities to honor or not to honor those communities. Observability tools and BGP routing monitoring can help answer key questions such as:
- Are my no-export communities being respected?
- Are my traffic engineering tags achieving the desired path selection?
- Have any new or unintended communities been introduced?
By analyzing community propagation patterns over time, teams can gain insight into policy compliance, inter-provider coordination, and the potential misconfigurations or policy drift that may occur.
In this way, communities can be a powerful indicator of operational health and policy enforcement across distributed networks.
Track AS path changes over time
The AS path of a particular route is a fundamental piece of information that describes the path that traffic must take to reach its destination. Some shifting of the AS path is expected over time. However, frequently shifting AS paths and particular patterns of path shifting can reveal underlying issues. Obtaining historical visibility of AS path changes over time is an essential component of a BGP routing monitoring strategy.
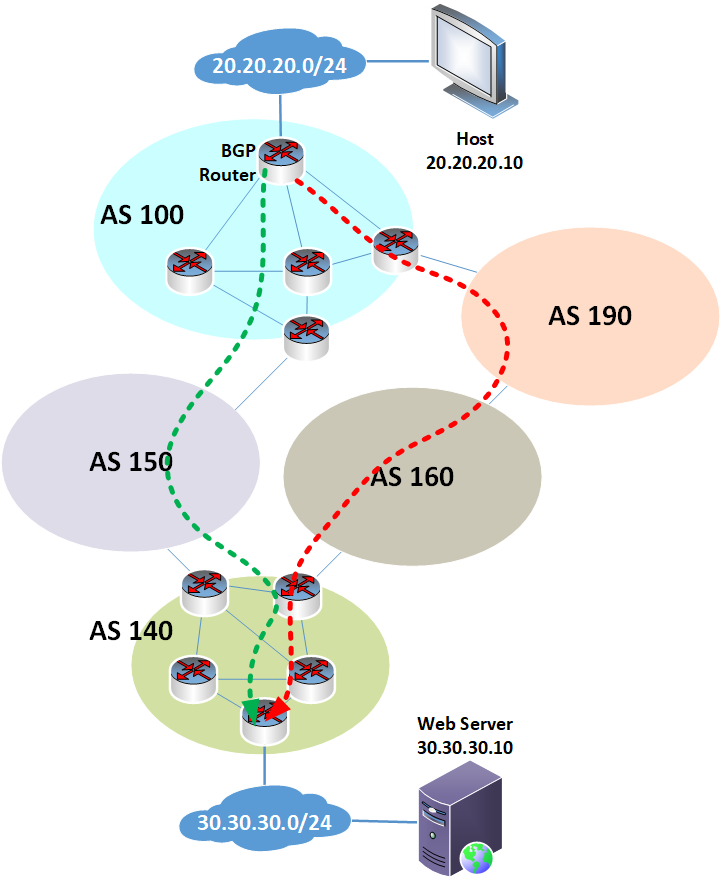
AS path baselining is used to obtain a baseline of expected AS path behavior for particular prefixes. The expected frequency and type of change are recorded during regular operation. All subsequent behaviors are then compared to this baseline to determine if a specific behavior indicates an abnormal or unexpected event.
Intelligent agents throughout a wide area, including within the core network and the network edge, are needed to observe AS path changes from various vantage points.
Unexpected AS path changes can indicate a variety of events, including:
- Network congestion or outages
- BGP routing policy changes
- Hijacks or peering disputes
- Route leaks
Monitoring BGP routing plays a crucial role in mitigating route path deviations and ensuring AS path integrity.Catchpoint’s article on BGP security emphasizes the crucial importance of monitoring in addressing these and many other similar events
Last thoughts
Intelligent monitoring is a cornerstone of ensuring security, resilience, and performance for BGP routing. Monitoring BGP reachability from the edge and enforcing reliable and well-maintained route filtering are foundational practices that must not be overlooked. Detecting route flaps, securing sessions, and validating route origins are equally critical in defending against some of the most disruptive routing failures and attacks. Leveraging BGP communities and tracking AS path changes further strengthens BGP routing integrity, control, and visibility across multi-provider environments.
All of this is only achievable using intelligent agents such as those implemented by Catchpoint, which provide deep, distributed, and real-time observability into the global routing fabric. By delivering insights from the edge and across diverse networks, these agents empower operators to detect issues proactively, validate policies, and maintain a stable and trustworthy Internet experience for users worldwide.

