The Domain Name System (DNS) is one of the most important technologies used on the Internet and in networking in general. This is the system that translates IP addresses into human-friendly domain names, also called Uniform Resource Locators (URLs), so that people can access websites more easily. DNS is necessary because humans are much better at being able to remember something like catchpoint.com than they are at memorizing an IP address—especially since IPv6 addresses are 128 bits long!
Because DNS has been an essential technology for years, it has also been looked at closely by hackers trying to find attack vulnerabilities. One of the most damaging types of DNS attack is known as DNS tunneling.
What Is DNS Tunneling?
DNS tunneling is a type of attack exploiting the Trojan horse concept where hackers embed malicious code or programs into a message that appears to be a DNS request. Since DNS is an essential component of most network and internet activity, this type of traffic is often able to pass through firewalls and other systems without much scrutiny.
The following is a basic outline of how a DNS attack is conducted:
- Register a Host Domain: A hacker registers a domain and may even put up a legitimate-looking site. On this site, the hacker will also have DNS tunneling malware programs installed and ready to be distributed when accessed.
- Infect a Target Computer with Malware: The next step, which is often the most difficult, is to get a computer within the target network infected with malware. This can be done in many different ways, including using other infected websites, infected emails, or even compromised hardware brought into a company’s facility.
- Connect Infected Computer to the Hacker’s Website: When ready, the infected computer will attempt to connect to the hacker’s website. Part of this connection is sending a DNS request to locate that website. DNS requests are always allowed to go through firewalls, giving the hacker a basic connection into the otherwise protected systems.
- Pass Malicious Code Through DNS Resolver: Once a connection is established and approved, the hacker’s host server can pass additional code or programs into the target network. This code can be used to collect data, place programs onto systems, or do any number of other things that can allow the long-term exploitation of the compromised systems.
Here is a basic diagram of how this process works:
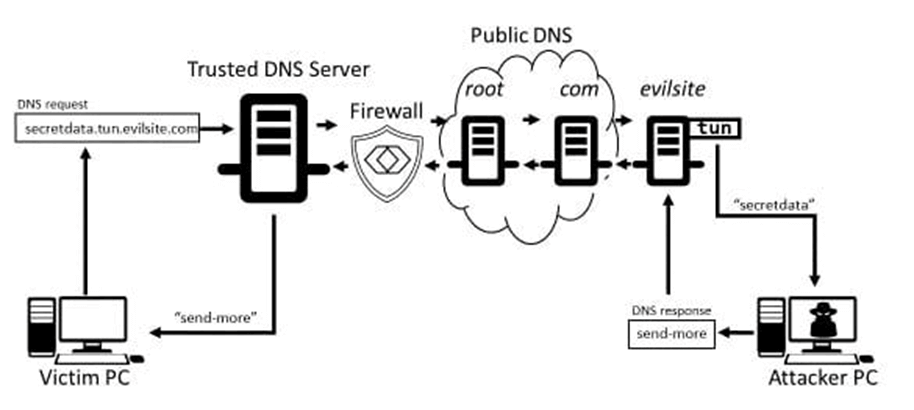
Attacks Related to DNS Tunneling
One of the most important things to note about DNS tunneling attacks is that the hackers don’t generally perform this type of attack as an end goal. Instead, they use a successful DNS tunneling attack as a way to complete other malicious acts. In addition, unlike some other types of hacking, the actual DNS tunneling action is not the first step in the attack.
DNS tunneling should be seen more as a hacking tool or strategy that is used as a part of other malicious activities. The following are some types of attacks that are often associated with DNS tunneling.
While these are some of the most common types of attacks that are related to DNS tunneling, they are far from the only ones. Almost every type of hacking attempt can benefit from either putting malware in place or being able to exploit a connection. This is why DNS tunneling toolkits are among the most commonly used resources for advanced hackers.
How to Detect a DNS Tunneling Attack
Detecting a DNS tunneling attack can be difficult. Fortunately, there are ways to identify when this type of attack is happening so that you can take action to stop it.
The first step in detecting a DNS tunneling attack is making sure that you are using an advanced antivirus/antimalware program, which is essential for avoiding most types of security threats. Beyond that, you need to make sure that you have systems in place that will perform deep scans of all traffic, including DNS requests.
These tools need to look at all types of traffic coming in and out of the network These tools should look for behavior like unusual destinations for traffic as well as spikes in traffic, and they should examine what is being transmitted to see if anything is out of the ordinary.
The size of the request and response can help reveal a suspicious DNS tunneling attempt. Since extra bytes are inserted in the packet header as part of DNS tunneling, monitoring the ratio of the bytes used in the source field to the bytes used in the destination field can help detect a suspicious activity. Detection tools capture the packets, store the byte counts, and measure the ratio looking for an usual change.
Another technique used for detecting suspicious DNS tunneling activity is to count the number of characters used in the label field (up to 63 characters) or the name field (up to 255 characters) of the DNS requests. DNS tunneling uses the label and name fields to transfer data back and forth as part of the DNS requests and responses.
Another option to consider is setting up and managing your own private DNS servers. Most internet connections rely on public DNS servers, which generally work well, but are outside your control. When you run your own DNS servers, you can have access to much more information related to sites that are accessed, redirected traffic, suspicious patterns, and much more.
{{banner-3="/design/banners"}}
DNS Monitoring Tools
As you might expect, DNS monitoring tools are critical for trying to detect DNS tunneling attacks. DNS traffic is unique in that while it is generally very small in size, it is also extremely important. In addition, virtually every connection to the Internet involves some type of DNS traffic at some point. This means that the DNS traffic is routed and secured differently than other types of network traffic, which makes it vulnerable to attack.
How to Protect Your Network Against DNS Tunneling
The best thing that you can do to protect your network against DNS tunneling is to make sure you have a comprehensive security plan in place. Since this type of attack not only requires the external attacker to have the right tools but also an infected device inside the network, protection will require a number of different steps. Some key mechanisms that you should have in place to minimize your risk of a DNS tunneling attack include the following:
- Updated Virus and Malware Protection: A good antivirus and antimalware strategy is absolutely essential for any corporate network. Using a proven system, and keeping it updated, will help to stop DNS tunneling attacks before they begin by preventing systems from being infected.
- Advanced Network Traffic Monitoring: Advanced network traffic monitoring tools look for all types of potentially malicious traffic, including DNS packets. This will help to identify this type of attack very early on so that it can be stopped.
- Network Insight Tools: Use these tools to look not just for what type of traffic is going through your network but also how much of it is important. Long-term monitoring of all types of network traffic will help your tools to be able to better identify changes and take actions to stop any unauthorized activity.
- Employee Training: The weakest point in any computer system is the set of behaviors of humans accessing the network. Keep your systems safe from DNS tunneling attacks by training your employees to avoid clicking on unapproved links, opening suspicious email, and taking other actions that could invite malware.
{{banner-sre="/design/banners"}}
Take Steps to Prevent a DNS Tunneling Attack
DNS tunneling attacks have been around for a long time, and they will continue to be a serious threat long into the future. If you are responsible for any type of corporate network or system with any valuable information, taking steps to prevent this type of attack is much easier than trying to stop an attack in progress. Take the time today to understand how DNS tunneling attacks work and how they can be stopped.