DNS Flood
Understanding and Preventing DNS Flood Attacks
On October 21, 2016, hundreds of major media and application service providers experienced outages, including some of the biggest in the world: Amazon, GitHub, PlayStation Network, Twitter, and PayPal. These services continued to have issues throughout the day, resulting in millions of dollars in lost revenue.
The common element among them was DYN, a DNS provider for all of these companies’ domains; its DNS servers had been targeted by what would later be identified as a DNS flood attack. This was one of the first major events that would expose glaring vulnerabilities in one of the services at the very heart of the Internet: the Domain Name System.
DNS floods are distributed denial of service (DDoS) attacks targeting DNS servers. In this article, we will explore how a DNS flood works, the types of DNS flood attacks that exist, the effects of a DNS flood, how a hypothetical attack is carried out, and best practices for preventing DNS flood attacks.
{{banner-26="/design/banners"}}
Summary of key DNS flood concepts
Here is a quick rundown of some of the key points covered in this article.
How a DNS flood works
Understanding (distributed) denial of service attacks
To understand how DNS floods work, it is important to first discuss the origins of the denial of service (DoS) attack and the distributed DoS (DDoS) variant.
A denial of service attack is one where a single point of origin—one IP address—targets a resource, attempting to take it down by flooding it with requests and thus preventing the server from being able to respond to legitimate queries. A distributed denial of service attack has multiple points of origin (with multiple IP addresses) that work in concert to attack a resource; typically, these are devices created or controlled through malicious methods. These attacks use various types of requests and protocols to overwhelm the resources of other devices; ICMP and UDP packets are popular for these attacks through IP address spoofing.
DNS flood: A DNS DDoS
DNS is the protocol responsible for translating domain names into IP addresses, which allows users to access websites and other resources on the Internet. A DNS flood attack is essentially a DDoS attack targeting the DNS infrastructure using DNS query and response traffic.
In a DNS flood attack, the attacker overwhelms DNS servers with a large volume of DNS queries or responses, causing them to slow down or crash. This can lead to website downtime, slow Internet speeds, and other disruptions. DNS flood attacks can be launched from networks of compromised devices, such as botnets, making them difficult to trace and stop.
{{banner-23="/design/banners"}}
Types of DNS flood attacks
There are several types of DNS flood attacks. Each is named for the specific techniques used to carry out the attack and has a unique element in how it functions.
Amplification/reflection attacks
An amplification/reflection attack begins with an attacker spoofing the IP address of the client to be the IP address of the victim (reflection), which results in all of the DNS replies being sent directly to the victim (amplification). The initial requests are very small and ask for the DNS servers to return the entire list of available DNS records for a particular domain, including subdomains. The resulting answer is substantially larger than the request: 100 times larger, in some cases.
If a threat actor has compromised only a few machines, all of which are spoofing their IPs and sending responses to the victim, the resulting traffic would be substantial enough to tie up the victim’s resources for servicing requests, which could no longer be processed.
This attack is significantly more effective if several DNS resolvers are targeted and have configurations that allow any source IP address.
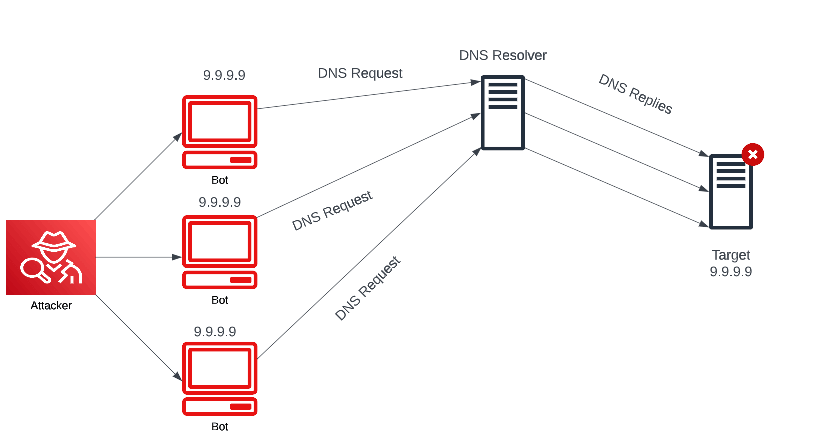
A real-world example of a DNS amplification attack occurred in March 2013, when the anti-spam organization Spamhaus was targeted by what was described as the largest DDoS attack in history at the time. The attack, which peaked at 300 gigabits per second, caused widespread disruption to Internet services and lasted for several days.
The attackers sent small DNS queries to vulnerable servers, which then responded with large DNS responses. The attackers spoofed the source IP addresses of the queries, making it appear as if the requests came from Spamhaus’s servers. The large volume of traffic generated by the DNS responses overwhelmed these servers, causing them to crash and making it difficult for legitimate traffic to reach the site. The attack was eventually mitigated by redirecting traffic through cloud-based DDoS protection services.
The Spamhaus attack demonstrated the potential of DNS amplification attacks to cause significant disruption to Internet capabilities.
{{banner-24="/design/banners"}}
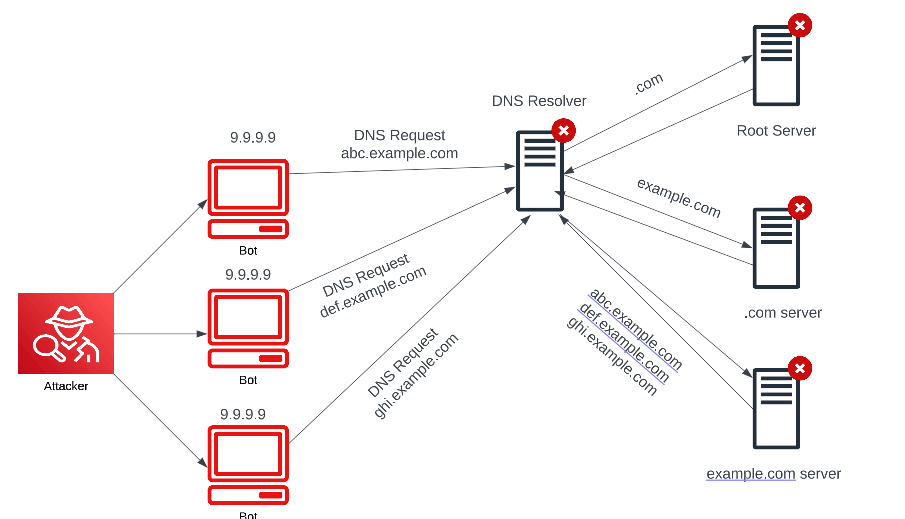
Water torture / NXDOMAIN attacks
This type of attack involves sending a large volume of DNS queries for valid domain names but with randomized subdomains. These requests cause the DNS server to repeatedly search for nonexistent subdomains. The nonexistent domain replies (NXDOMAIN) will cause cache overflow errors, and the server will no longer be able to process requests for legitimate domains.
The term “water torture” is used to describe this type of attack because it is analogous to the constant dripping of water on a victim’s forehead—in this case, the victim being the DNS server. This sort of attack is not sudden or explosive but rather a slow and methodical process that can, nonetheless, be just as damaging in the long run as a more sudden attack.
In the diagram below, an attacker is trying to target example.com and will cause a cache overflow to the authoritative name server and any resolvers used by the bots. Requests for numerous nonexistent subdomains of example.com (abc, def, and ghi) will move through the resolver and then the root, .com, and authoritative DNS servers. The authoritative name server will respond with NXDOMAIN, and the resolver’s cache will start to overflow while the authoritative server is losing resources processing the requests and trying to return the NXDOMAIN responses.
NXDOMAIN attacks and the Passion botnet
A Radware Cybersecurity Advisory dated January 31, 2023, highlighted the emergence of a Russian botnet called Passion. Affiliated with groups like Killnet and Anonymous Russia, Passion offers “DDoS-as-a-service” to pro-Russian hacktivists. The botnet was recently used in attacks on medical institutions in multiple countries as retaliation for their support of Ukraine. The Passion group is known for defacement and denial-of-service attacks against individuals and organizations opposing the Russian invasion of Ukraine.
Radware warns that the Passion botnet was used in cyberattacks deployed on January 27, 2023, which targeted medical institutions in the US, Portugal, Spain, Germany, Poland, Finland, Norway, Netherlands, and the UK.
These attacks prompted the Health Sector Cyber Security Coordination (H3C) center to release several reports warning the healthcare industry against NXDOMAIN attacks and other floods. More information can be found in this H3C white paper and this sector alert specifically addressing the tactics used in the NXDOMAIN attacks.
Effects of a DNS flood attack
A DNS flood can produce a wide range of significant negative impacts on both the targeted network and its users. These include both direct and indirect effects, such as the following:
- Service disruption: The primary impact of a DNS flood attack is the disruption of the targeted network or website services. The high volume of DNS requests generated by the attack can overload the network’s DNS servers, causing them to become unresponsive and preventing legitimate users from accessing the services.
- Slow response times: In addition to outright service disruption, a DNS flood attack can also cause slow response times for users attempting to access the targeted network or website. Excessive load on DNS servers can cause delays in the DNS resolution process, resulting in slow page load times and similar effects.
- Reputation damage: If users are unable to access the services they need, they may become frustrated and look for alternative providers, which can damage the reputation of the targeted organization.
- Financial loss: Having users be unable to access services can result in substantial revenue losses through lost sales on inoperable ecommerce sites, canceled subscriptions, and refund requests.
- Distraction: In some cases, a DNS flood attack may be used as a smokescreen to cover up other malicious activities, such as data theft or unauthorized access to the targeted network or website. This can result in significant data compromise, further damage to the organization’s reputation, and financial losses.
Creating a DNS flood attack
To help you better understand how DNS flood attacks work, let’s discuss how, in theoretical terms, a DNS flood attack is created and executed.
How targets are chosen
Threat actors may choose a target for DNS attacks based on several factors, including the target’s industry, size, reputation, and vulnerabilities. Understanding the common considerations that threat actors take into account when choosing a target for DNS attacks can help you better assess your organization’s risk level:
- Industry: Some industries, such as finance, healthcare, and government, are more likely to be targeted by DNS attacks due to the sensitivity of their data and the potential impact of an attack. For example, a threat actor may target a bank’s DNS server to gain access to customer account information.
- Size: Large organizations with complex IT infrastructures may be more vulnerable to DNS attacks because they have more entry points for an attacker to exploit. On the other hand, small businesses may also be targeted due to their limited security resources.
- Reputation: Threat actors may target organizations with significant public profiles, such as well-known brands or government agencies, to gain attention or publicity for their actions.
- Known vulnerabilities: Organizations with known vulnerabilities in their DNS infrastructures may become attractive targets for attackers. Vulnerabilities can include unpatched software, weak passwords, or misconfigured servers.
- Relationships: Threat actors may target an organization’s DNS infrastructure to gain access to other organizations with whom they have a business relationship, such as partners or suppliers.
- Willingness to pay a ransom: An organization is more likely to be attacked if threat actors perceive a willingness on the part of its leadership to pay a ransom.
Creating the attack
For simplicity, this section will focus on an amplification attack executed against an imaginary DNS provider. Our attacker will need to secure additional computing resources to carry out the attack by sending requests, which could be accomplished by following these steps:
- The attacker creates a fake domain name that looks similar to a very popular website, like ƒacebook.com. Pay close attention to the “f” character in “ƒacebook” here—this is not a normal “f” but actually the function symbol (“ƒ”), copied from the Windows-1252 character set. (In this case, the domain actually appears as “www.xn--acebook-w1b.com” when viewed in a browser. ICANN’s explanation of international domain names provides further information on the conversion that occurs when you use these sorts of esoteric symbols.)
- The attacker sets up a web server that hosts a website for the fake domain that resembles the real Facebook site.
- The attacker distributes content with a link to the page, enticing people to try to visit the fake Facebook site.
- Typically, a very convincing login prompt will ask for credentials and a user enters them, not realizing they are being captured in plain text. Machines that have fallen victim to the attack will become “bots” now under the control of the attacker.
The attacker will now start generating DNS requests for a specific domain (to respond with the full list of records) from each device. The dig command (a Linux-based domain lookup command) is an example of how this could be accomplished: Each dig command issued on a device will create the required queries. Each machine must appear to be sending the requests from the victim’s IP, which is accomplished by spoofing the source IP in the header to be the IP for the victim.
If all goes according to plan, the attack should successfully consume most of the resources of the victim responsible for resolving DNS requests. Sites hosted with the provider will begin to return 501 errors.
Again, this is all very basic and hypothetical. Another option is simply purchasing a “premade” attack from a blacklisted website. Of course, this is unethical and should not be attempted by anyone, but the attacks do exist in this form, so organizations need to recognize this as a possible concern.
{{banner-25="/design/banners"}}
Best practices for preventing and addressing DNS flood attacks
Preventing DNS flood attacks requires a multi-layered approach that involves a combination of network infrastructure and application-level security measures. Some of the best practices for preventing DNS flood attacks include the following:
- Implementing rate limiting: Rate limiting is a technique that restricts the volume of DNS requests that can be processed by a DNS server. By restricting the number of requests that can be processed, organizations can reduce the risk of DNS flood attacks and ensure that legitimate requests are prioritized. DNS resolvers can be set to limit DNS queries with “ANY” source. It is also possible to limit repeated queries for nonexistent domains.
- Using access control lists (ACLs): Access control lists can be used to restrict access to DNS servers and prevent unauthorized requests from reaching the server, reducing the risk of DNS flood attacks. It is common practice to use ACLs to prevent traffic from external countries that are high-level points of origin for cyberattacks, when applicable.
- Enabling DNS caching: DNS caching can help reduce the number of requests that need to be processed by a DNS server. By caching frequently requested DNS records, organizations can reduce the load on their DNS servers and reduce the risk of DNS flood attacks. Note that this should only be used with rate limiting in place in order to avoid NXDOMAIN cache overflows.
- Monitoring DNS traffic: Regular monitoring of DNS traffic can help organizations identify unusual patterns or spikes in traffic that may indicate a DNS flood attack. Catchpoint’s Internet Performance Monitoring platform includes alerts that are paramount in addressing DNS attacks in real time.
- Distributing DNS services: DNS services should never have a single point of failure because redundancy and placement are key factors in maintaining operations during any flood attack. At the very least, two DNS servers containing business-critical DNS records should be in operation, located in different geographical locations (virtual or physical).
- Keeping DNS software up to date: Staying up to date with the latest security patches and updates can help prevent known vulnerabilities from being exploited in DNS flood attacks.
- Using DNSSEC: Domain Name System Security Extensions (DNSSEC) is a security-enhancing protocol for DNS that provides the ability to authenticate DNS responses.
In addition to following these best practices, organizations should also have a comprehensive incident response plan in place to quickly detect and respond to DNS flood attacks. This plan should include procedures for notifying internal and external stakeholders as well as steps for mitigating the impact of the attack and restoring services as quickly as possible.
Summary of key concepts
DNS floods are essentially DDoS attacks targeting DNS servers. In this article, we explained how these attacks work, described the different types of DNS floods, and discussed their potential effects. To help you appreciate just how simple it can be to acquire bots and target someone in this manner, we also provided context by looking at how an attack can be set up from the perspective of a potential attacker. This information should help you understand the potential severity and scalability of these dangers.
We also provided a list of best practices for preventing DNS flood attacks, including rate limiting, ACLs, caching, monitoring, distributed DNS, regular updates, and DNSSEC. By following best practices and maintaining a proactive approach to DNS security, you can reduce the risk of DNS flood attacks and protect your network and users from the impact of cybercrime.