DNS Poisoning Attacks
A Free Guide to Understanding DNS Poisoning Attacks
As the world becomes increasingly reliant on the Internet for communication, commerce, and collaboration, the vulnerabilities within its architecture become more apparent. Among these vulnerabilities, Domain Name System (DNS) cache poisoning emerges as a formidable adversary, capable of orchestrating cyberattacks that deceive, disrupt, and compromise the security of online interactions.
This article delves into the depths of DNS poisoning attacks, shedding light on the relevant mechanisms, potential consequences, and strategies that can be employed to defend against this insidious threat.
Summary of key DNS poisoning attack concepts
The table below summarizes the key concepts covered in this article.
What is DNS cache poisoning?
DNS cache poisoning involves the manipulation of Domain Name System (DNS) records to misrepresent the trustworthiness of the key information that DNS provides. At its core, DNS cache poisoning misleads the system by injecting false data into the caches of DNS resolvers, the crucial intermediaries responsible for translating human-friendly domain names into machine-understandable IP addresses.
By infiltrating these caches with inaccurate IP mappings, malicious actors can redirect unsuspecting users to fraudulent websites, intercept sensitive communications, and potentially pave the way for further cyber incursions. This subtle technique exposes the vulnerability inherent in the foundational layers of digital communication, highlighting the critical importance of understanding and mitigating the risks posed by DNS attacks.
How a DNS poisoning attack works
In this attack, an attacker selects a target domain to poison, which could belong to a popular website, a critical service, or any other resource that users are likely to access. Next, a DNS query is sent to a vulnerable recursive DNS resolver, which is responsible for resolving domain names on behalf of users. A vulnerable resolver with an empty cache will forward the query to attempt to get an authoritative server’s response. Simultaneously, the attacker sends multiple forged responses to the resolver, claiming to be the authoritative server (spoofed IP), each with a different source port and transaction ID. For the poisoning to be successful, the transaction ID and source port need to match the original query and arrive before the actual authoritative server's response is received by the resolver.
The attacker’s forged responses contain misleading information associating the target domain with a malicious IP address controlled by the attacker. These responses are designed to closely resemble legitimate DNS responses to increase the chances of successful poisoning.
If one of the attacker’s forged responses reaches the resolver before the legitimate response, the resolver updates its cache with the incorrect IP address for the target domain, thereby “poisoning” it. The attacker has now gained control over the traffic intended for the legitimate domain.
This is the key point of DNS cache poisoning: Users querying the resolver will now be directed to the malicious IP address instead of the legitimate one. This could potentially lead to phishing, data interception, or malware distribution.

The Kaminsky bug
The Kaminsky bug, discovered by security researcher Dan Kaminsky in 2008, exposed the vulnerabilities within DNS that made cache poisoning attacks possible. This bug exploited a weakness in how DNS servers handled and validated information related to domain names and IP addresses. As described above, this vulnerability could allow malicious actors to manipulate the information stored in DNS caches, redirecting users to malicious websites without their knowledge or consent. This redirection could lead to various types of cyberattacks, including phishing, malware distribution, and data theft.
Here are the specific vulnerabilities that Kaminsky was able to expose through his analysis:
- Limited transaction ID space: DNS queries and responses include a transaction ID to match a response with its corresponding query. The transaction ID was only 16 bits in size, so there were only 65,536 possible values. This limited space made it feasible for attackers to guess the correct transaction ID that a DNS resolver was expecting.
- Fixed DNS query source port: DNS queries are sent from a source port on the resolver to a destination port on a DNS server. In the original DNS specification, the source port was fixed to be port 53, which made it predictable and thus susceptible to spoofing.
- Transaction ID guessing: The Kaminsky bug leveraged the combination of the limited transaction ID space and the fixed source port. An attacker could flood a DNS resolver with a massive number of DNS responses, each with a different transaction ID but the same source port. The attacker aimed to predict the correct transaction ID and send a response that would match a legitimate query made by the DNS resolver.
- DNS response forgery: In a typical DNS response, the attacker’s DNS server would send a falsified response with the malicious IP address for a legitimate domain. If the attacker’s response arrived at the DNS resolver before the legitimate response, it could be cached by the resolver.
- Short TTLs and retry strategies: Authoritative DNS servers typically employ time-to-live (TTL) values for cached records. However, some DNS servers used very short TTLs and aggressive retry strategies, making them even more vulnerable to cache poisoning.
The rest of this article looks at the detection, remediation, and prevention of DNS poisoning attacks. This discussion is framed using an example that simulates a real-world DNS cache poisoning attack (the Kaminsky bug) and the steps that can be taken to detect, remediate, and prevent such an attack. Our example uses the fictitious company IT Wizard to demonstrate the process of detecting, remediating, and preventing continued DNS cache poisoning attacks against a real-world domain.
Detection
In our scenario, IT Wizard employees are seeing a strange home page when connecting to the primary website, itwizard.cloud, and have reported the issue to the IT team to request assistance. Initial descriptions suggest a possible DNS cache poisoning attack.
Detecting DNS cache poisoning can be challenging, but there are several signs and symptoms to watch for.
Unusual website redirects
As in our example, one of the most common signs of DNS cache poisoning is when users are redirected to unexpected or malicious websites when they try to access legitimate ones. For example, they may be redirected to phishing sites or malicious servers.
Here is the expected landing page of itwizard.cloud:

In our scenario, here is what employees are seeing:

It is pretty clear at this point that some type of redirect has been configured.
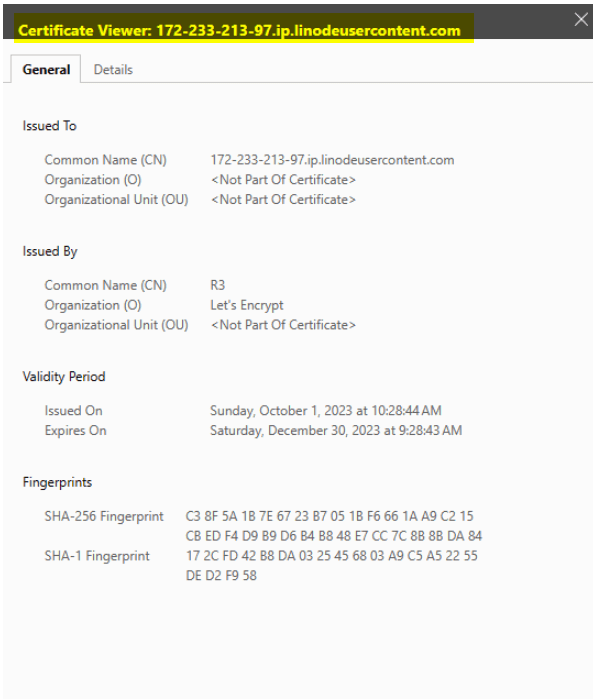
SSL/TLS certificate mismatches
If a website’s SSL/TLS certificate doesn’t match the domain name it claims to be associated with, this can indicate a DNS cache poisoning attack. Browsers often display warning messages about certificate mismatches.
In our case, this is the expected security certificate.
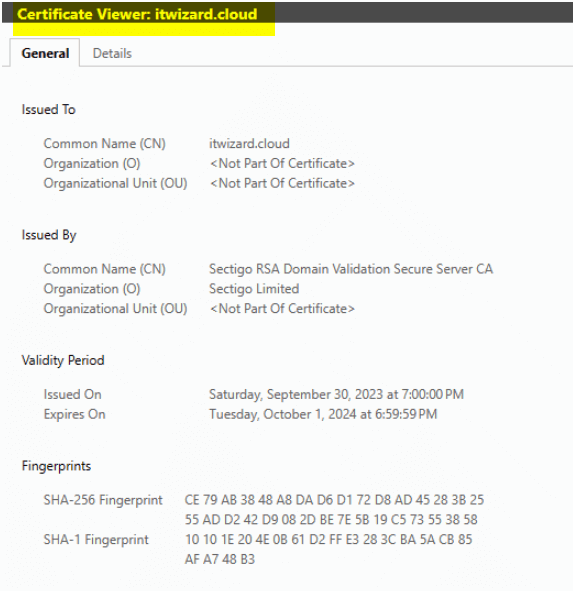
This is the certificate after the website is redirected.
Unexpected DNS records
Check the DNS records of a domain name. If you notice unexpected or unauthorized changes in DNS records (e.g., A records or CNAME records), this could be a sign of a DNS poisoning attack.
For our example, here’s a previous capture of the nslookup command displaying the proper A name record for itwizard.cloud.
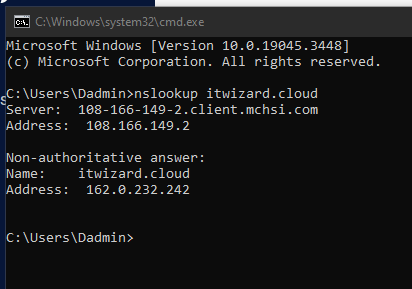
Here’s how it looked after issues started to be reported.

DNSSEC validation failures
If your DNS infrastructure supports DNS Security Extensions (DNSSEC), validation failures can indicate DNS cache poisoning. DNSSEC helps ensure the integrity of DNS responses.
Remediation
If you suspect that your DNS cache has been poisoned or compromised, remediating the DNS poisoning attack is crucial to restoring the integrity and security of your DNS infrastructure. This could include the following steps.
Change back DNS records
In our example, the attack clearly changed DNS records to invalid values chosen by the attackers. The immediate remediation step for IT Wizard would include changing the DNS records back to their correct values. In the event that the records had been hosted with a major DNS provider, additional steps might be required to make the changes. In most cases, the admin interface for the provider will allow the records to be rolled back to the original values, but admin credentials should be changed as well.
Isolate the affected DNS servers
Immediately disconnect or isolate the DNS servers that you suspect have been compromised. This will prevent further poisoning of its cache and protect other DNS servers in your network.
Flush the DNS cache
Flush the DNS cache on the affected servers to remove any poisoned or malicious DNS entries. The method for flushing the cache depends on your DNS server software.
Patch vulnerable systems
Identify and patch any other vulnerable systems or software within your network that may have been exploited during the attack.
Monitor for ongoing attacks
Implement real-time monitoring and intrusion detection systems to detect and prevent future DNS cache poisoning attempts. Continuously monitor DNS traffic and log any suspicious activity.
Prevention
IT Wizard could have taken several precautions to prevent this DNS cache poisoning attacks, including the following:
Patch DNS software
Keep your DNS server software up to date with the latest security patches. Vendors regularly release updates to address vulnerabilities, including those related to DNS cache poisoning attacks.
Implement DNSSEC
If you haven’t already done so, implement DNSSEC to add an extra layer of security to your DNS infrastructure. DNSSEC helps prevent cache poisoning attacks by digitally signing DNS records.
Use source port randomization
Configure your DNS server to use random source ports for outgoing DNS queries. This makes it more difficult for attackers to predict and spoof the source port in DNS responses.
Employ response rate limiting (RRL)
Enable RRL on your DNS server to limit the rate at which it sends responses to specific client IP addresses. RRL can help mitigate DNS amplification attacks and slow down cache poisoning attempts.
Network segmentation
Segment your network to isolate critical DNS infrastructure from less trusted parts of your network. Network segmentation can help contain attacks and limit their impact.
Use monitoring and logging
Set up comprehensive monitoring and logging for DNS traffic and server activities. Use intrusion detection systems (IDS) and regularly review DNS query logs to detect and respond to suspicious behavior. Certain services, like Catchpoint, will be effective for monitoring queries across resolvers globally, not just within the company's environment. DNS resolvers forwarding requests outside the network can be easily compromised and internal monitoring solutions would not be able to detect poisoning.
Consider redundancy and failover methods
Implement redundancy and failover mechanisms for your DNS infrastructure to ensure continuous service availability even in the event of an attack or server failure.
Conduct regular security audits and assessments
Regular formal reviews of your DNS infrastructure can enable your organization to identify and remediate vulnerabilities. Penetration testing can help discover potential weaknesses.
Stay informed
Keep up to date about emerging DNS vulnerabilities and security best practices. Subscribe to security mailing lists and follow updates from industry sources and security organizations.
Educate personnel
Educate your IT staff and end-users about DNS security best practices and the importance of verifying DNS responses.
Look at third-party DNS services
Consider using third-party DNS services that provide additional security features and protection against cache poisoning attacks.
Summary
Understanding DNS poisoning attacks is critical in safeguarding online interactions and maintaining the integrity of digital communication. DNS poisoning attacks involve manipulating DNS records to misrepresent the trustworthiness of the information they provide. Attackers inject false data into DNS resolver caches, redirecting users to fraudulent websites and intercepting sensitive communications.
The Kaminsky bug exposed DNS vulnerabilities that allowed cache poisoning. The bug leveraged limited transaction IDs, predictable source ports, and DNS response forgery to redirect users to malicious sites.
Detection methods include looking for unusual website redirects, SSL/TLS certificate mismatches, unexpected DNS record changes, and DNSSEC validation failures.
Remediation steps include correcting invalid DNS records, isolating the affected DNS server, flushing the DNS cache, reviewing and restoring DNS records, changing DNS server credentials, patching vulnerable systems, and monitoring for ongoing attacks.
There are many potential prevention strategies, including patching DNS software, using DNSSEC, source port randomization, employing response rate limiting (RRL), instituting network segmentation, monitoring, conducting security audits, staying informed, using third-party DNS services, ensuring redundancy and failover, and educating personnel on DNS security best practices. Platforms like Catchpoint will provide a robust solution for all of the DNS monitoring inside and outside an organizations' network, allowing for a single point of management and alerting.